Unknown TA targetting Russia
Introduction
→ This post analyzes a multi-stage campaign that targets Russian MoD,FSB and other government based instituions. The campgaign was observed throughout 2025 that uses a Rust-built PE with a ZIP overlay to deliver a multi-file dropchain and ultimately install a remote-access backdoor via UltraVNC.
First Stage
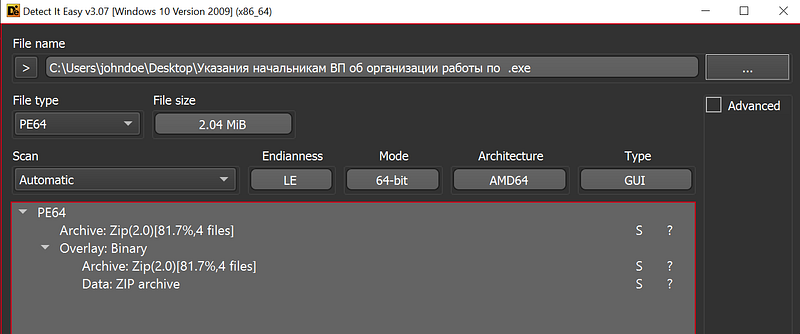
→ The file we’re going to be looking today at is a file called “Указания начальникам ВП об организации работы по .exe” which translates to “Instructions to heads of the VP on organizing work”. As we can see it has a Zip overlay which contains 4 files and the file masquerades with a PDF icon. We can either get the zip from the resources or we can see how the zip file is being dropped.
- One important thing to note is that this binary is made in rust
- Since we’re primarily interested in the next stages we can look at the import section and jump right away into debugger to see where and what files are being dropped.
→ The list of import gives us an idea as to what we can expect from the sample. Functions like CreateProcessW alongside CreateToolhelp32Snapshot is a classic combo for process injection. The VirtualProtect call confirms it. Anti debugging tricks using the AddVectoredExceptionHandler. We also see some calls for file related imports, such as MapViewOfFile and CreateFileW, which align perfectly with its observed function of unzipping and writing it to disk.
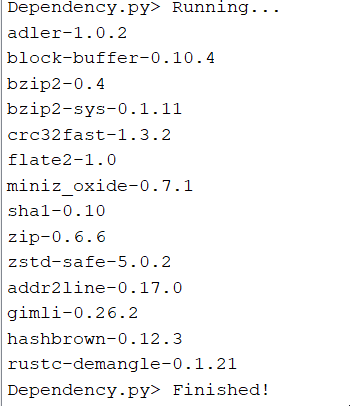
→ We can extract all the dependencies using a ghidra script. As expected, the zip crate is present, directly enabling its primary function of decompressing the ZIP overlay. It also contains other libraries like flate2, bzip2 which suggests it may handle other compression files as well. More on that later.
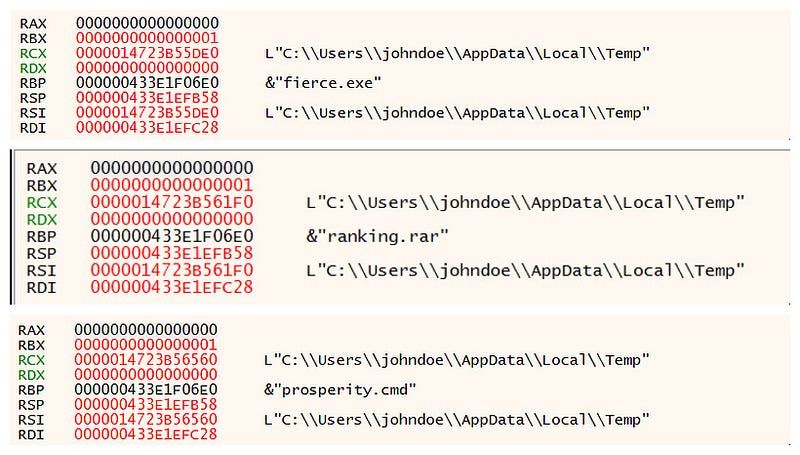
→ Looking into the debugger we can see 3 files are being dropped and a pdf file with the same name as the exe is being opened.
→ At the end of program we see a powershell command being ran. It uses ping to delay the execution. It runs prosperity.cmd with hidden window parameter.
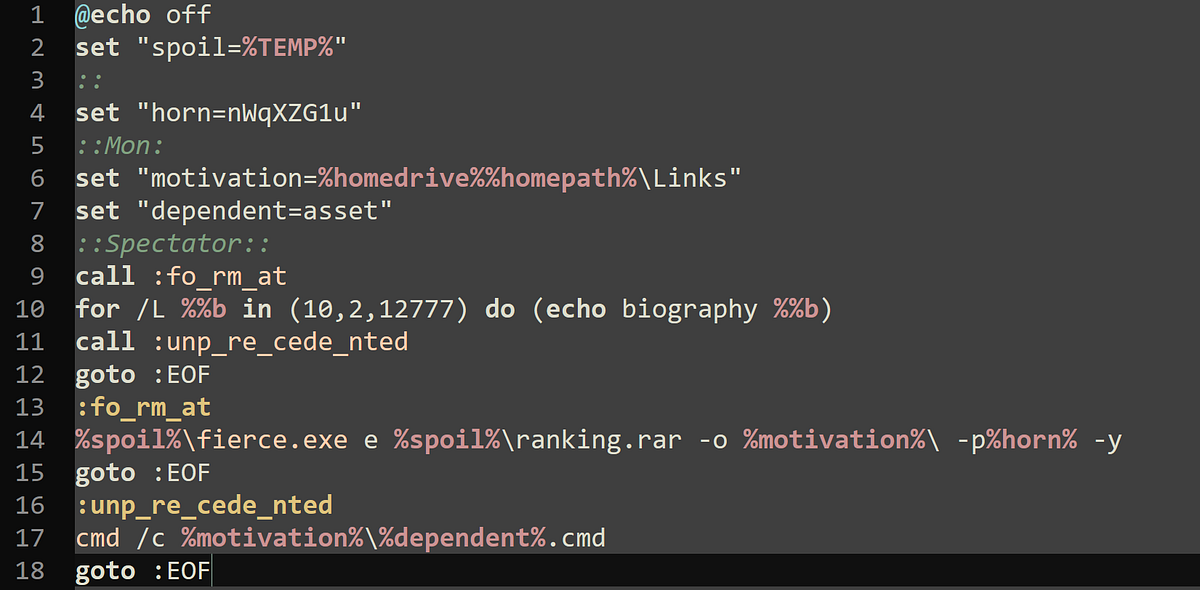
Second Stage
→ The script starts by setting some variables to point to the user’s Temporary and Links directory. There is a for loop which prints biography as sequence of numbers to delay the execution. The 2 subroutines work as follows
- The first subroutine fo_rm_at uses fierce.exe from the system’s temporary directory to extract a file named ranking.rar into the user’s Links folder, using the password stored in %horn%.
- After extraction, it calls the second subroutine unp_re_cede_nted, which launches a command prompt to execute a newly unpacked file named asset.cmd.
fierce.exe is just a portable command line rar extractor
Third Stage
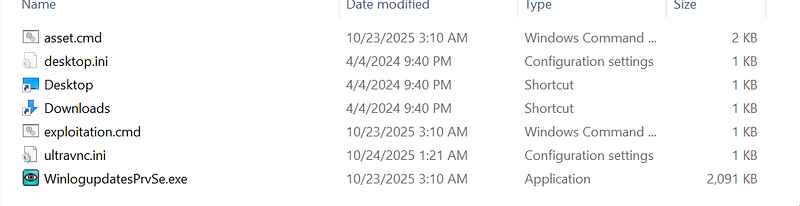 ranking.rar extracted → The rar file contains 4 files and we can look at the asset.cmd file.
ranking.rar extracted → The rar file contains 4 files and we can look at the asset.cmd file.
→ The asset.cmd starts off by enabling delayed variable expansion and sets the path to pointing to …\Links\cheer and calls int_act to build the UltraVNC configuration file. Next up it calls the su_cce_ssi_ve subroutine which runs exploitation.cmd right away.
→ Finally the c_ra_ck subroutine is used to setup persistence.The scheduled task called NvNodeLauncher will repeatedly run the helper script at every 2 minutes, ensuring the helper keeps executing.
exploitation.cmd
→ The final batch file sets up and constructs the filename ,force-stops any running instance of WinlogupdatesPrvSe.exe.
→ The rec_r_uit subroutine runs three nslookup calls with short pauses to beacon the C2 server.
→ s_u_pp_l_e_m_en_t subroutine composes a quoted argument string (which expands to things like -autoreconnect, -connect vdaliot.ru:443, an ID that includes the local %COMPUTERNAME%, and a -run flag) and launches the WinlogupdatesPrvSe.exe from *…\Links* using powershell Start-Process with those arguments.
Attribution
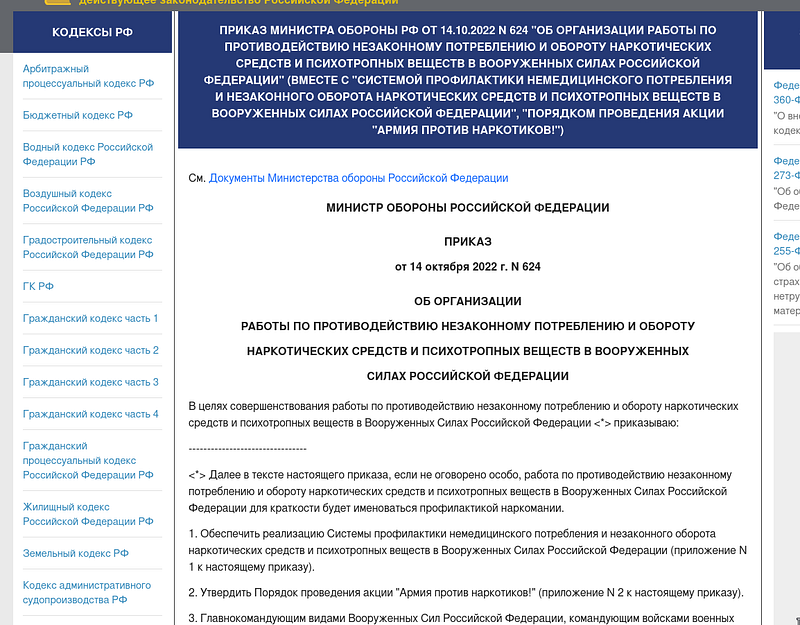
→ The decoy document used in this attack is an official Russian MoD order on combatting the use of narcotics and substance abuse in the military. After some research we were able to find the original document used in the attack published on the official sites. Here you can find the many other documents which are used in past months as decoys.
→ In recent one more decoy document using the same TTPs arised and it targetted the ministry of investigative departments of joint group forces. Instead of using UltraVNC, a Go backdoor was employed that had similar use case. This document surfaced at starting of October 2025.
→ Another old document that was previously used in 2017-2020 resurfaced using the same TTP as the one we discussed above. 
→ The newly-reported “GamaCopy” campaign explicitly mimics Gamaredon tactics but swaps Ukrainian lures for Russian-language ones. Vendors like KnownSec (and recorded-future) notes GamaCopy’s spear-phishing archives contain “official reports” of Russian documents and deploy payloads via 7zSFX and UltraVNC. GamaCopy is likely a false-flag linked to another state actor (“Core Werewolf”), but it does use Russian decoy documents.
Based on reported TTPs, we assess Paper Werewolf/GOFFEE as a top candidate (high confidence); HellHounds and GamaCopy/CoreWerewolf are also plausible (medium confidence) since they use Russian doc lures. Gamaredon or Ghostwriter are less likely here (low confidence), as they typically prey on Ukrainian/Belarus targets. (Public attribution to APT28/29 is unsupported; those GRU/SVR-linked actors generally do not use Russian-internal MoD orders as lures.)
IOCs
1
2
soon
Thanks for reading this analysis! ❤️
Feel free to connect with me on:
Discord: somedieyoungzz
Twitter: @IdaNotPro